Last update images today Application Programming Interface Attacks













.jpg)















https www practical devsecops com wp content uploads 2024 01 API Security Challenges 980x541 png - Top 5 API Security Challenges In 2024 Practical DevSecOps API Security Challenges 980x541 https techxmedia com wp content uploads 2024 02 Untitled design 2024 02 29T121405 422 png - Trend Micro Predicts AI Driven Attacks Surge In 2024 TECHx Media Untitled Design 2024 02 29T121405.422
https clerk com next image - January 2024 Vulnerability Update Imagehttps www deepseas com wp content uploads 2024 01 cyber threats 2024 blog scaled jpg - A Cyber Year In Review Look Ahead Cybersecurity In 2023 2024 Cyber Threats 2024 Blog Scaled https protectai com hubfs PAI Threat 3 Jan 2024 png - Protect AI S January 2024 Vulnerability Report PAI Threat 3 Jan 2024
https miro medium com v2 resize fit 1024 1 bJz6VYHaYF4VpRvOWHDDzA jpeg - Can AI Replace Cybersecurity In 2024 A Battle Of Code And Chrome 1*bJz6VYHaYF4VpRvOWHDDzA https appnovi com wp content uploads 2023 11 Ethan Smart Blog ASM Part 2 1024x435 png - Evolving Attack Surface Management For 2024 Risk Prioritization AppNovi Ethan Smart Blog ASM Part 2 1024x435
https www itgovernance co uk blog wp content uploads 2024 03 image 10 png - Global Data Breaches And Cyber Attacks In 2024 IT Governance UK Blog Image 10
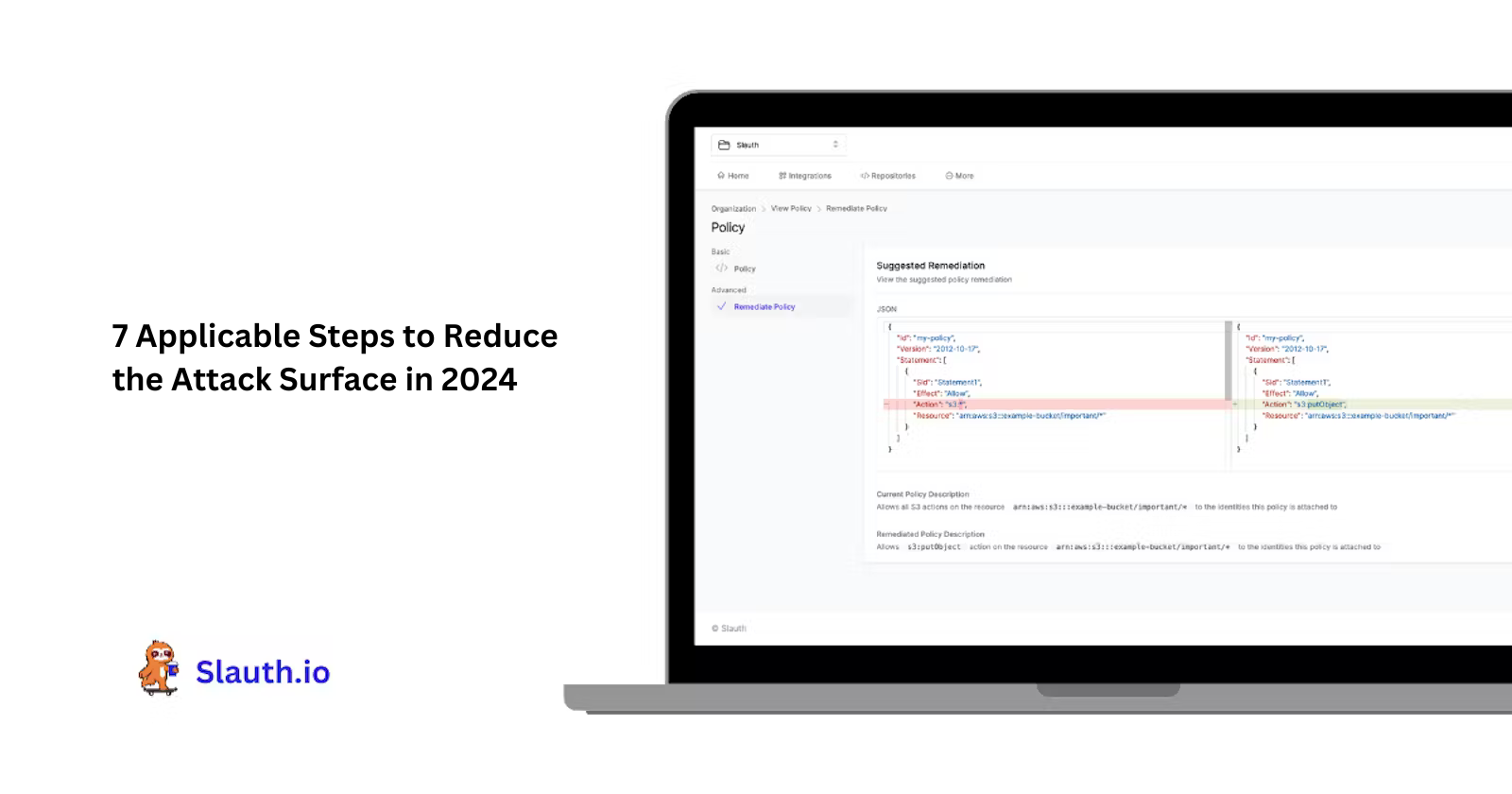
https cdn hashnode com res hashnode image upload v1701053303957 35847112 053d 48b7 b491 dea2478235d7 png - 7 Applicable Steps To Reduce The Attack Surface In 2024 Slauth Io 35847112 053d 48b7 B491 Dea2478235d7 https www rampart ai com hubfs Navigating The Future Application Security Challenges And Strategies For 2024 png keepProtocol - Navigating The Future Application Security Challenges And Strategies Navigating The Future Application Security Challenges And Strategies For 2024 #keepProtocol
https base binus ac id wp content uploads 2024 02 CyberAttack2024 gif - 8 Serangan Siber Tertinggi 2024 BINUS School Of Engineering CyberAttack2024 https static wixstatic com media 639273 0290df7cac044ddbb767efbdff6704ed mv2 jpg v1 fill w 1024 h 683 al c 639273 0290df7cac044ddbb767efbdff6704ed mv2 jpg - Phishing Attacks In 2024 Identifying And Preventing In A Virtual 639273 0290df7cac044ddbb767efbdff6704ed~mv2
https miro medium com v2 resize fit 1200 1 Rv03NOKZIksfEkhuuY DWg jpeg - Ransomware Threats In 2024 Trends Predictions And Prevention 1*Rv03NOKZIksfEkhuuY DWg https sensorstechforum com wp content uploads 2024 03 New Loop DoS Attack Based on CVE 2024 2169 in UDP Protocol 1024x585 jpg - Cyber News Articles On Cybersecurity Malware Online Privacy New Loop DoS Attack Based On CVE 2024 2169 In UDP Protocol 1024x585 https techlooters com wp content uploads 2023 12 Protect Yourself from Cyber Attacks in 2024 png - Cyber Attack 2024 What Will Happened In 2024 Techlooters Com Protect Yourself From Cyber Attacks In 2024
https dataconomy com wp content uploads 2024 02 CVE 2024 21893 Ivanti vulnerability 2024 768x430 jpg - CVE 2024 21893 Ivanti Vulnerability 2024 Explained Dataconomy CVE 2024 21893 Ivanti Vulnerability 2024 768x430 https img game news24 com 2024 01 The 2024 attack will begin for Square Enix s use of AI aggressively jpeg - The 2024 Attack Will Begin For Square Enix S Use Of AI Aggressively The 2024 Attack Will Begin For Square Enix S Use Of AI Aggressively
https img s msn com akamaized net tenant amp entityid AA1mqAXX img - Tech Expert Warns 2024 Will See Explosion Of AI Powered Cybercrime AA1mqAXX.img
https cdn hashnode com res hashnode image upload v1701053303957 35847112 053d 48b7 b491 dea2478235d7 png - 7 Applicable Steps To Reduce The Attack Surface In 2024 Slauth Io 35847112 053d 48b7 B491 Dea2478235d7 https techlooters com wp content uploads 2023 12 Protect Yourself from Cyber Attacks in 2024 png - Cyber Attack 2024 What Will Happened In 2024 Techlooters Com Protect Yourself From Cyber Attacks In 2024
https www traceable ai wp content uploads 2024 02 webinar api security 2024 png - API Security In 2024 The Critical Crossroads Is Here Traceable API Webinar Api Security 2024 https www vincacyber com wp content uploads 2024 01 What Are the Top 10 Cybersecurity Trends and Challenges for 2024 2 400x400 jpg - How To Prevent Network Attacks Using AI And Machine Learning Vincacyber What Are The Top 10 Cybersecurity Trends And Challenges For 2024 2 400x400
https blogger googleusercontent com img b R29vZ2xl AVvXsEj3Q84AXoKBGOQ0EYJ H8xs5b Qh6kRz H06FDfBmkHo O7F9irWHcEYMUSu3PKjfdVClupPP0ZjlMSkI2Bjy662iEsZSwG IxXWIdxW s1bFvCQCx D3xAZ 80Qg eWe ziCalLdRFluYh2BYLOuRR6yTO22EcsRFWVn3otjSdN8W60dsp8RXVX0afGEo s1600 RVS 01 2024 png - Data Breaches Digest Ransomware Operator Claims Week 1 2024 RVS 01 2024 https www rampart ai com hubfs Navigating The Future Application Security Challenges And Strategies For 2024 png keepProtocol - Navigating The Future Application Security Challenges And Strategies Navigating The Future Application Security Challenges And Strategies For 2024 #keepProtocolhttps img nomios com images Brand content Photography Industries wireless payment retail smartphone jpg - API Security Trends 2024 Nomios Nederland Wireless Payment Retail Smartphone
https protectai com hubfs PAI Threat 3 Jan 2024 png - Protect AI S January 2024 Vulnerability Report PAI Threat 3 Jan 2024 https sensorstechforum com wp content uploads 2024 03 New Loop DoS Attack Based on CVE 2024 2169 in UDP Protocol 1024x585 jpg - Cyber News Articles On Cybersecurity Malware Online Privacy New Loop DoS Attack Based On CVE 2024 2169 In UDP Protocol 1024x585
https socprime com wp content uploads CVE 2024 23204 1 768x450 jpg - CVE 2024 23204 Detection Exploitation Of A Recently Patched CVE 2024 23204 1 768x450